Difference between revisions of "MoVfuscator Writeup"
(Created page with "==Intro== Three days ago Chris Domas [https://twitter.com/xoreaxeaxeax/status/629446810243694592 announced] the release of M/o/Vfuscator2, a beautiful single instruction C com...") |
m |
||
| Line 8: | Line 8: | ||
Coincidentally we published a new attack against white-boxes a few days ago: [https://eprint.iacr.org/2015/753 Differential Computation Analysis: Hiding your White-Box Designs is Not Enough]. |
Coincidentally we published a new attack against white-boxes a few days ago: [https://eprint.iacr.org/2015/753 Differential Computation Analysis: Hiding your White-Box Designs is Not Enough]. |
||
| − | <br>M/o/Vfuscator2 doesn't transform your AES into a traditional white-box but we should admit it's quite intimidating. |
+ | <br>M/o/Vfuscator2 doesn't transform your AES into a traditional white-box based on look-up tables but we should admit it's quite intimidating for a reverser. |
==Visualization== |
==Visualization== |
||
<br>For example, here is a trace of the initial AES, up to the first three rounds: |
<br>For example, here is a trace of the initial AES, up to the first three rounds: |
||
| Line 20: | Line 20: | ||
<br> |
<br> |
||
<br>Ouch! That's why I limited the trace to the first 3 rounds, it's so huge that I've disk space and RAM issues to display more... |
<br>Ouch! That's why I limited the trace to the first 3 rounds, it's so huge that I've disk space and RAM issues to display more... |
||
| + | <br>The black square is simply the main MOV loop repeating all long, so if there is information, it should be in the memory accesses. |
||
| + | ==Challenge== |
||
| + | The initial tiny-AES128-C example encrypts a fixed plaintext with a fixed key but let's make a more realistic challenge where one can provide arbitrary plaintexts. |
||
| + | |||
| + | <source lang=c> |
||
| + | #include <stdio.h> |
||
| + | #include <string.h> |
||
| + | #include <stdint.h> |
||
| + | #define CBC 0 |
||
| + | #define ECB 1 |
||
| + | #include "aes.h" |
||
| + | |||
| + | static const uint8_t *CHRHEX = (uint8_t *) |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\x00\x01\x02\x03\x04\x05\x06\x07\x08\x09\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\x0A\x0B\x0C\x0D\x0E\x0F\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\x0A\x0B\x0C\x0D\x0E\x0F\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \ |
||
| + | "\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"; |
||
| + | |||
| + | static void phex(uint8_t* str) |
||
| + | { |
||
| + | unsigned char i; |
||
| + | for(i = 0; i < 16; ++i) |
||
| + | printf("%.2x", str[i]); |
||
| + | printf("\n"); |
||
| + | } |
||
| + | |||
| + | int main(int argc, char *argv[]) |
||
| + | { |
||
| + | uint8_t key[16] = { 0x2b, 0x7e, 0x15, 0x16, 0x28, 0xae, 0xd2, 0xa6, 0xab, 0xf7, 0x15, 0x88, 0x09, 0xcf, 0x4f, 0x3c }; |
||
| + | uint8_t plaintext[16]; |
||
| + | uint8_t ciphertext[16]; |
||
| + | int n=0; |
||
| + | const char *p; |
||
| + | const uint8_t *D; |
||
| + | uint8_t c=0, e, *d; |
||
| + | p = argv[1]; |
||
| + | d = plaintext; |
||
| + | D = (d + sizeof (plaintext)); |
||
| + | for (; d != D && *p; p++) { |
||
| + | e = CHRHEX [(int) *p]; |
||
| + | if (e != 0xFF) { |
||
| + | c = ((c << 4) | e); |
||
| + | n++; |
||
| + | if (n == 2) { |
||
| + | *(d++) = c; |
||
| + | n = 0; |
||
| + | } |
||
| + | } |
||
| + | } |
||
| + | AES128_ECB_encrypt(plaintext, key, ciphertext); |
||
| + | printf("plaintext:\n"); |
||
| + | phex(plaintext); |
||
| + | printf("ciphertext:\n"); |
||
| + | phex(ciphertext); |
||
| + | return 0; |
||
| + | } |
||
| + | </source> |
||
Revision as of 13:23, 10 August 2015
Intro
Three days ago Chris Domas announced the release of M/o/Vfuscator2, a beautiful single instruction C compiler leveraging the paper "mov is Turing-complete" (pdf), by Stephen Dolan.
That's it, once compiled, your program is made only of MOV instructions.
See the REcon 2015 slides (pdf) for more insight.
The code is available here: https://github.com/xoreaxeaxeax/movfuscator and by default check.sh will apply it on https://github.com/kokke/tiny-AES128-C , a small portable AES128 implementation.
So, is it safe to protect your AES crypto with M/o/Vfuscator2?
Coincidentally we published a new attack against white-boxes a few days ago: Differential Computation Analysis: Hiding your White-Box Designs is Not Enough.
M/o/Vfuscator2 doesn't transform your AES into a traditional white-box based on look-up tables but we should admit it's quite intimidating for a reverser.
Visualization
For example, here is a trace of the initial AES, up to the first three rounds:
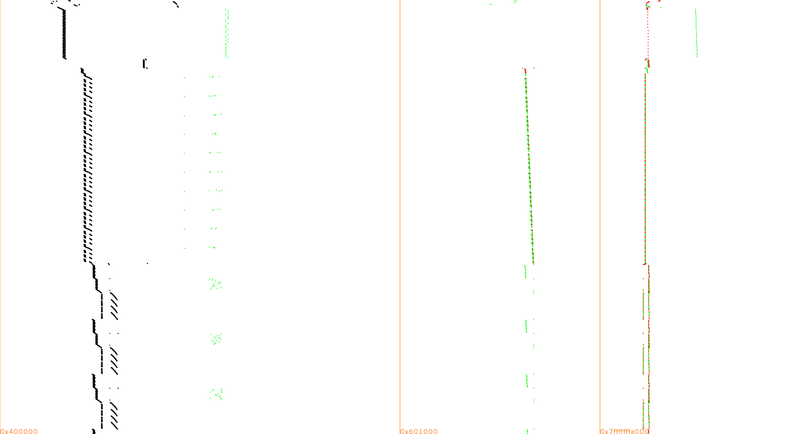
Same convention as in our paper: memory range on the X-axis, time counting from top to bottom on the Y-axis, instructions in black, mem reads in green, mem writes in red.
And here once it's compiled with M/o/Vfuscator2

Ouch! That's why I limited the trace to the first 3 rounds, it's so huge that I've disk space and RAM issues to display more...
The black square is simply the main MOV loop repeating all long, so if there is information, it should be in the memory accesses.
Challenge
The initial tiny-AES128-C example encrypts a fixed plaintext with a fixed key but let's make a more realistic challenge where one can provide arbitrary plaintexts.
#include <stdio.h>
#include <string.h>
#include <stdint.h>
#define CBC 0
#define ECB 1
#include "aes.h"
static const uint8_t *CHRHEX = (uint8_t *)
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\x00\x01\x02\x03\x04\x05\x06\x07\x08\x09\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\x0A\x0B\x0C\x0D\x0E\x0F\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\x0A\x0B\x0C\x0D\x0E\x0F\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF" \
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF";
static void phex(uint8_t* str)
{
unsigned char i;
for(i = 0; i < 16; ++i)
printf("%.2x", str[i]);
printf("\n");
}
int main(int argc, char *argv[])
{
uint8_t key[16] = { 0x2b, 0x7e, 0x15, 0x16, 0x28, 0xae, 0xd2, 0xa6, 0xab, 0xf7, 0x15, 0x88, 0x09, 0xcf, 0x4f, 0x3c };
uint8_t plaintext[16];
uint8_t ciphertext[16];
int n=0;
const char *p;
const uint8_t *D;
uint8_t c=0, e, *d;
p = argv[1];
d = plaintext;
D = (d + sizeof (plaintext));
for (; d != D && *p; p++) {
e = CHRHEX [(int) *p];
if (e != 0xFF) {
c = ((c << 4) | e);
n++;
if (n == 2) {
*(d++) = c;
n = 0;
}
}
}
AES128_ECB_encrypt(plaintext, key, ciphertext);
printf("plaintext:\n");
phex(plaintext);
printf("ciphertext:\n");
phex(ciphertext);
return 0;
}